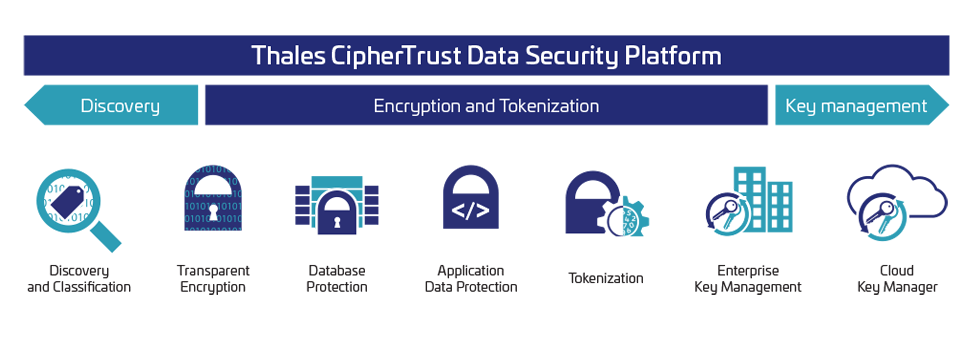
Sophos Central Device Encryption 1-Year Subscription License for Business | Technology Solutions for Small and Medium Business

Super Security Safe Deposit Box Anti theft Lock With Encryption Keys Copper Cylinder|Lock Cylinders| - AliExpress
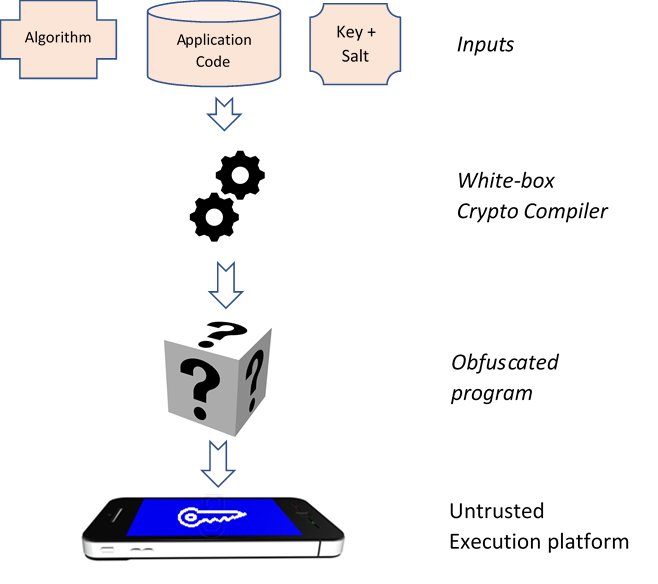
How White-box Cryptography is gradually eliminating the hardware security dependency | by Terugu Venkat | Engineering Ezetap | Medium